Hi Jeff
Thanks for above im sure it will help someone in the future, your previous posts directed me to learning more about the docker networks and I came across the user-defined network which has the following advantage:
User-defined bridges provide automatic DNS resolution between containers .
User-defined bridges provide better isolation .
So this is what I did:
Create a monitoring network
docker network create --driver bridge monitoring
Add the following to my docker-compose.yml for Librenms
networks:
default:
external:
name: monitoring
Edited my docker-compose.yml of oxidized to look from this which is at the following link GitHub - ytti/oxidized: Oxidized is a network device configuration backup tool. It's a RANCID replacement!
docker-compose.yml
docker-compose file example for oxidized that will start along with docker daemon
oxidized:
restart: always
image: oxidized/oxidized:latest
ports:
- 8888:8888/tcp
environment:
CONFIG_RELOAD_INTERVAL: 600
volumes:
- /etc/oxidized:/root/.config/oxidized
to this
version: “3.5”
services:
oxidized:
image: oxidized/oxidized:latest
ports:
- target: 8888
published: 8888
protocol: tcp
environment:
- “CONFIG_RELOAD_INTERVAL=600”
volumes:
- /dockers/oxidized:/root/.config/oxidized
restart: always
networks:
default:
external:
name: monitoring
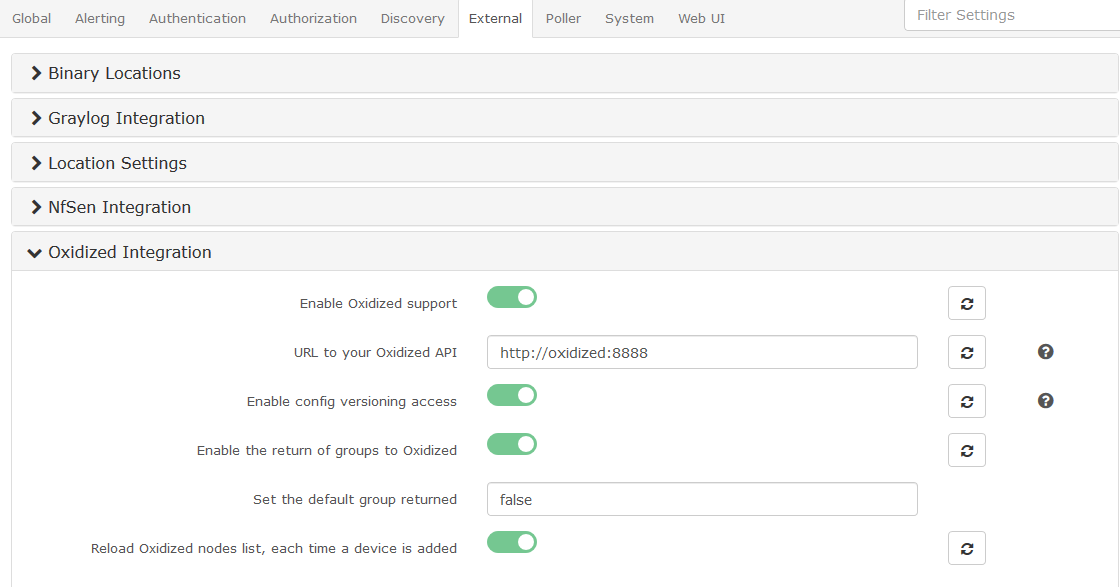
I then started my librenms and oxidized docker and configured librenms as following
Generated an API Key in librenms
and edited my config file for oxidized
rest: 0.0.0.0:8888
output:
default: git
git:
user: Oxidized
email: [email protected]
repo: " /root/.config/oxidized/default.git"
source:
default: http
http:
url: http://librenms:8000/api/v0/oxidized
scheme: http
delimiter: !ruby/regexp /![]()
user: username
pass: password
map:
name: hostname
model: os
username: username
password: password
group: group
vars_map:
enable: enable
headers:
X-Auth-Token: ‘blahblahblahblahblahblahblahblahblahblahblah’
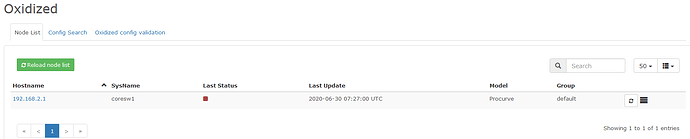
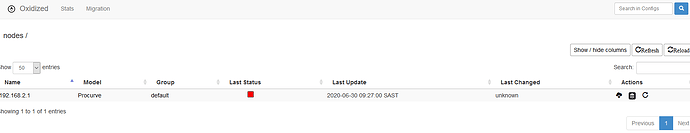
And it works
And on the oxidized web gui
For me this is resolved