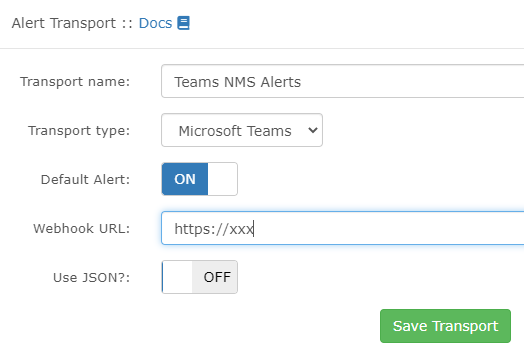
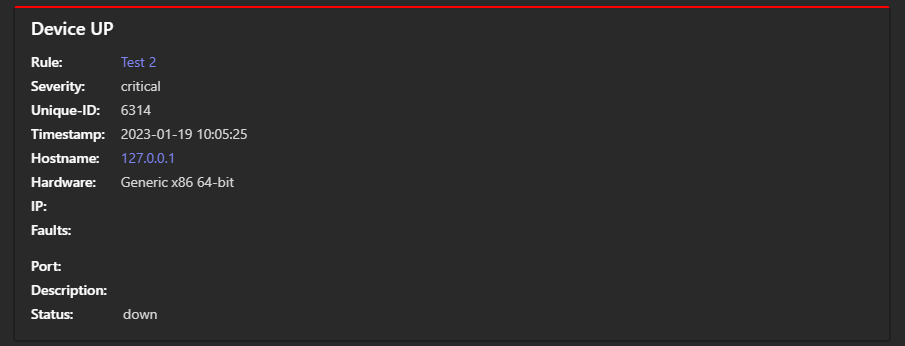
I was able to intercept the connection using the proxy of the Burp Suite Software:
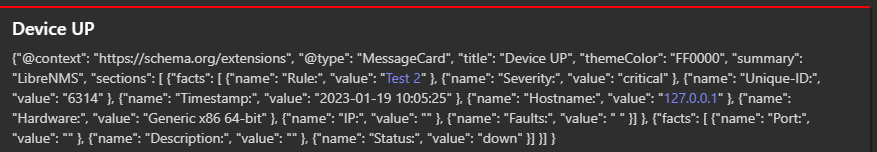
This is the payload I get with the json flag on:
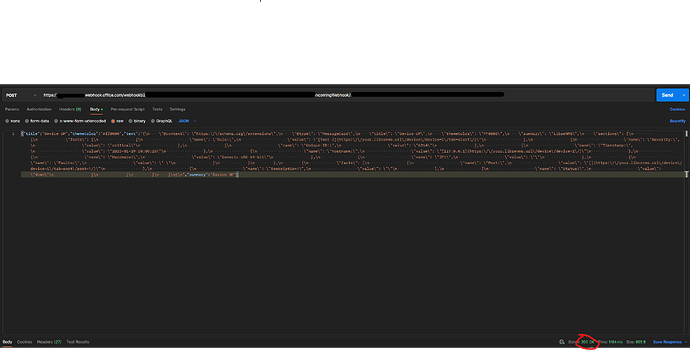
POST /webhookb2/XXXXXXXXXXXXXXXXXXXXX@cXXXXXXXXXXXXXXXXXXXX-XXXXXXXXXXXXXXXXX/IncomingWebhook/XXXXXXXXXXXXXXXXXXXXXXX/XXXXXXXXXXXXXXXXXXXX HTTP/2
Host: XXXXXXXXXXXXX.webhook.office.com
Accept: */*
Content-Length: 1728
Content-Type: application/x-www-form-urlencoded
{
"@context": "https://schema.org/extensions",
"@type": "MessageCard",
"title": "Device UP",
"themeColor": "FF0000",
"summary": "LibreNMS",
"sections": [
{
"facts": [
{
"name": "Rule:",
"value": "[Test 2](https://your.librenms.url/device/device=1/tab=alert/)"
},
{
"name": "Severity:",
"value": "critical"
},
{
"name": "Unique-ID:",
"value": "6314"
},
{
"name": "Timestamp:",
"value": "2023-01-19 10:05:25"
},
{
"name": "Hostname:",
"value": "[127.0.0.1](https://your.librenms.url/device/device=1/)"
},
{
"name": "Hardware:",
"value": "Generic x86 64-bit"
},
{
"name": "IP:",
"value": ""
},
{
"name": "Faults:",
"value": " "
}
]
},
{
"facts": [
{
"name": "Port:",
"value": "[](https://your.librenms.url/device/device=1/tab=port/port=/)"
},
{
"name": "Description:",
"value": ""
},
{
"name": "Status:",
"value": "down"
}
]
}
]
}
This is the payload I get using the json flag off:
POST /webhookb2/XXXXXXXXXXXXXXXXXXXX@XXXXXXXXXXXXXXXXXXXXXXXXX-XXXXXXXXXXXXXX/IncomingWebhook/XXXXXXXXXXXXXXXXXXXXXXX/XXXXXXXXXXXXXXXXXXXXX HTTP/2
Host: XXXXXXXXXXX.webhook.office.com
Accept: */*
Content-Length: 2000
Content-Type: application/x-www-form-urlencoded
{"title":"Device UP","themeColor":"#ff0000","text":"{\n \"@context\": \"https:\/\/schema.org\/extensions\",\n \"@type\": \"MessageCard\",\n \"title\": \"Device UP\",\n \"themeColor\": \"FF0000\",\n \"summary\": \"LibreNMS\",\n \"sections\": [\n {\n \"facts\": [\n {\n \"name\": \"Rule:\",\n \"value\": \"[Test 2](https:\/\/your.librenms.url\/device\/device=1\/tab=alert\/)\"\n },\n {\n \"name\": \"Severity:\",\n \"value\": \"critical\"\n },\n {\n \"name\": \"Unique-ID:\",\n \"value\": \"6314\"\n },\n {\n \"name\": \"Timestamp:\",\n \"value\": \"2023-01-19 10:05:25\"\n },\n {\n \"name\": \"Hostname:\",\n \"value\": \"[127.0.0.1](https:\/\/your.librenms.url\/device\/device=1\/)\"\n },\n {\n \"name\": \"Hardware:\",\n \"value\": \"Generic x86 64-bit\"\n },\n {\n \"name\": \"IP:\",\n \"value\": \"\"\n },\n {\n \"name\": \"Faults:\",\n \"value\": \" \"\n }\n ]\n },\n {\n \"facts\": [\n {\n \"name\": \"Port:\",\n \"value\": \"[](https:\/\/your.librenms.url\/device\/device=1\/tab=port\/port=\/)\"\n },\n {\n \"name\": \"Description:\",\n \"value\": \"\"\n },\n {\n \"name\": \"Status:\",\n \"value\": \"down\"\n }\n ]\n }\n ]\n}\n","summary":"Device UP"}
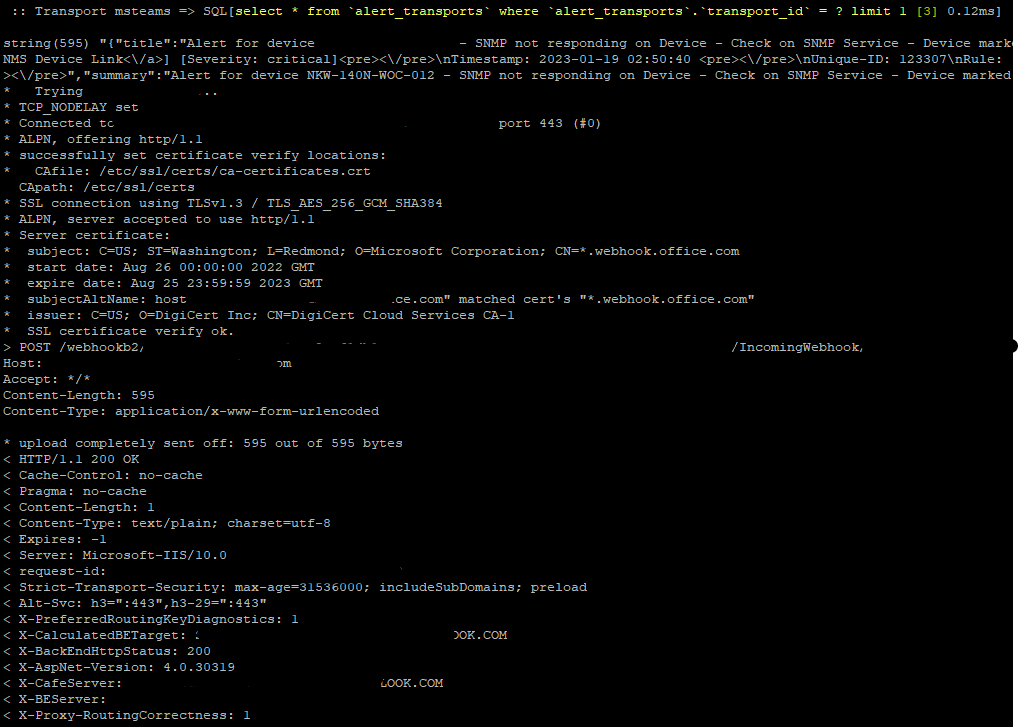
For both of them I get the same error:
string(456) "{"title":"DEVICE DOWN","themeColor":"#ff0000","text":"Device Name: librenms.xxx.xxx.xxx.xxx\nDevice Ip Address: 127.0.0.1\nDEVICE DOWN\nSeverity: critical\nTimestamp: 2023-01-19 00:41:07\nUnique-ID: 6263\nRule: TEST Faults:\n #1: sysObjectID = .1.3.6.1.4.1.8072.3.2.10; sysDescr = Linux librenms.xxx.xxx.xxx 3.10.0-1160.76.1.el7.x86_64 #1 SMP Wed Aug 10 16:21:17 UTC 2022 x86_64; location_id = 1; \nAlert sent to:\n","summary":"DEVICE DOWN"}"
* About to connect() to xxxxxxxxxxx.webhook.office.com port 443 (#0)
* Trying 52.96.166.242...
* Connected to xxxxxxx.webhook.office.com (52.96.166.242) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* SSL connection using TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
* Server certificate:
* subject: CN=*.webhook.office.com,O=Microsoft Corporation,L=Redmond,ST=Washington,C=US
* start date: Aug 26 00:00:00 2022 GMT
* expire date: Aug 25 23:59:59 2023 GMT
* common name: *.webhook.office.com
* issuer: CN=DigiCert Cloud Services CA-1,O=DigiCert Inc,C=US
> POST /webhookb2/7xxxxxxxxxxxxxxxxxxxxxxxx@xxxxxxxxxxxxxxxxxxxxxxxx-xxxxxxxxxxxxxx/IncomingWebhook/xxxxxxxxxxxxxxxxxxxxxxx/xxxxxxxxxxxxxxxxxxx HTTP/1.1
Host: xxxxxxxx.webhook.office.com
Accept: */*
Content-Length: 456
Content-Type: application/x-www-form-urlencoded
* upload completely sent off: 456 out of 456 bytes
< HTTP/1.1 400
< Content-Length: 49
< Content-Type: text/plain; charset=utf-8
< Server: Microsoft-IIS/10.0
< request-id: xxxxxxxxxxxxxxxxxxxxx
< Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
< Alt-Svc: h3=":443",h3-29=":443"
< X-PreferredRoutingKeyDiagnostics: 1
< X-CalculatedFETarget: xxxxxxxxxxx.internal.outlook.com
< X-BackEndHttpStatus: 400
< X-CalculatedBETarget: xxxxxxxxxxxxxxx.NAMPRD09.PROD.OUTLOOK.COM
< X-BackEndHttpStatus: 400
< X-End2EndLatencyMs: 1329
< X-RUM-Validated: 1
< X-RUM-NotUpdateQueriedPath: 1
< X-Proxy-RoutingCorrectness: 1
< X-MS-ForwardingCorrelationId: xxxxxxxxxxxxxxxxx
< X-Proxy-BackendServerStatus: 400
< X-BEPartition: xxxxxxxxxxxxxxxxxx
< X-FEProxyInfo: xxxxxxxxxxxxxxxxxxxxx.NAMPRD05.PROD.OUTLOOK.COM
< X-FEEFZInfo: SJC
< MS-CV: xxxxxxxxxxxxxxxxxxxxxxxxxxxx
< X-FEServer: SA1P222CA0014
< X-FirstHopCafeEFZ: SJC
< X-Powered-By: ASP.NET
< X-FEServer: xxxxxxxxxxxxxxxxxxxxxxxx
< Date: Thu, 19 Jan 2023 09:00:14 GMT
<
* Connection #0 to host xxxxxxxxxxxxxxxx.webhook.office.com left intact
string(43) "Microsoft Teams returned Error, retry later"
string(960) "HTTP/1.1 400
Content-Length: 49
Content-Type: text/plain; charset=utf-8
Server: Microsoft-IIS/10.0
request-id: 2f3bfee0-6c0a-6858-55e2-1d94d3405fa1
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
Alt-Svc: h3=":443",h3-29=":443"
X-PreferredRoutingKeyDiagnostics: 1
X-CalculatedFETarget: xxxxxxxxxxxxx.internal.outlook.com
X-BackEndHttpStatus: 400
X-CalculatedBETarget: xxxxxxxxxxxxxx.NAMPRD09.PROD.OUTLOOK.COM
X-BackEndHttpStatus: 400
X-End2EndLatencyMs: 1329
X-RUM-Validated: 1
X-RUM-NotUpdateQueriedPath: 1
X-Proxy-RoutingCorrectness: 1
X-MS-ForwardingCorrelationId: xxxxxxxxxxxxxxxxx
X-Proxy-BackendServerStatus: 400
X-BEPartition: xxxxxxxxxxxxxx
X-FEProxyInfo: xxxxxxxxxxxxxxxxxxxx.NAMPRD05.PROD.OUTLOOK.COM
X-FEEFZInfo: SJC
MS-CV: xxxxxxxxxxxxxxxxxxxxxxxxxxxxx
X-FEServer: SA1P222CA0014
X-FirstHopCafeEFZ: SJC
X-Powered-By: ASP.NET
X-FEServer: SJ0PR05CA0039
Date: Thu, 19 Jan 2023 09:00:14 GMT
string(49) "Bad payload received by generic incoming webhook."
ERRORSQL[insert into `eventlog` (`reference`, `type`, `datetime`, `severity`, `message`, `username`, `device_id`) values (?, ?, ?, ?, ?, ?, ?) [null,null,"2023-01-19 01:16:02",5,"Could not issue critical alert for rule 'TEST' to transport 'msteams'","",1] 0.18ms]
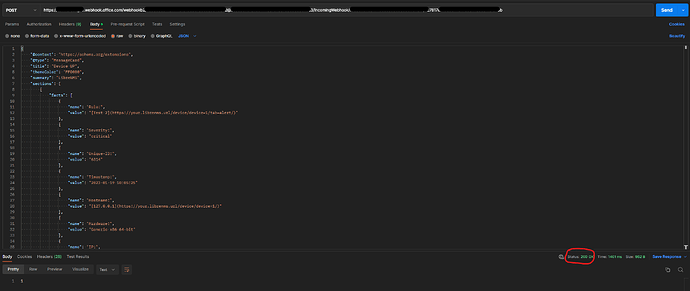
Now if I use postman to make the same two request, it works:
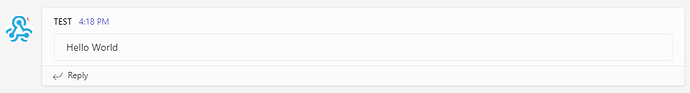
Json flag on
Postman
Teams
Json flag off
PostMan
Teams
Maybe there is a header missing or something like that, I am not a programmer so I can’t tell 
Thank you